Hit The DNS
Hit The DNS recon tool written in bash
Hit The DNS
Description
Hit-The-Dns is a modern DNS recon tool written in bash which will help you during the DNS recon similar to tools like subfinder or dnsenum.
Installation
1
wget https://raw.githubusercontent.com/juanbelin/Hit-The-Dns/refs/heads/main/hit-the-dns.sh
1
chmod +x hit-the-dns.sh
Example Usage
This example was done using Attacking DNS Lab from HTB Academy.
DNS Fuzzing
1
./hit-the-dns -d inlanefreight.htb -i 10.129.203.6 -w ~/seclists/Discovery/DNS/subdomains-top1million-110000.txt
DNS Fuzzing verbose mode
-v or --verbose in order to view fuzzing attempts.
1
./hit-the-dns -d test.com -i 10.129.203.6 -w ~/seclists/Discovery/DNS/subdomains-top1million-110000.txt -v
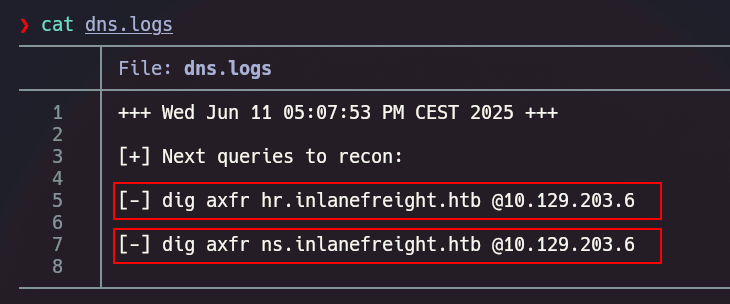
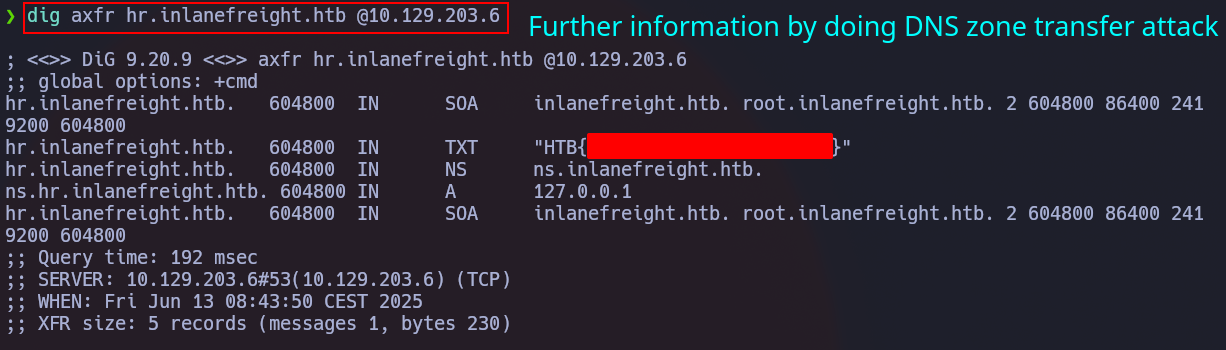
Checking dns.logs and following the next step
The dns.logs file will give you the next step in the recon (zone transfer attack) according with the subdmains that the tool has found during the fuzzing.
Usage
1
./hit-the-dns -d domain.com -i 10.10.2.15 -w /path/to/wordlist.txt <-v>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
./hit-the-dns.sh
█████ █████ ███ █████
░░███ ░░███ ░░░ ░░███
░███ ░███ ████ ███████
░███████████ ░░███ ░░░███░
░███░░░░░███ ░███ ░███
░███ ░███ ░███ ░███ ███
█████ █████ █████ ░░█████
░░░░░ ░░░░░ ░░░░░ ░░░░░
█████ █████ ██████████ ██████ █████ █████████
░░███ ░░███ ░░███░░░░███ ░░██████ ░░███ ███░░░░░███
███████ ░███████ ██████ ░███ ░░███ ░███░███ ░███ ░███ ░░░
░░░███░ ░███░░███ ███░░███ ░███ ░███ ░███░░███░███ ░░█████████
░███ ░███ ░███ ░███████ ░███ ░███ ░███ ░░██████ ░░░░░░░░███
░███ ███ ░███ ░███ ░███░░░ ░███ ███ ░███ ░░█████ ███ ░███
░░█████ ████ █████░░██████ ██████████ █████ ░░█████░░█████████
░░░░░ ░░░░ ░░░░░ ░░░░░░ ░░░░░░░░░░ ░░░░░ ░░░░░ ░░░░░░░░░
[+] Usage:
-d/--domain <domain> -w/--wordlist </path/to/wordlist> -i/--ip <IP>
-v/--verbose = Verbose mode
-h --> Show help panel
Do not forget adding the domain to the
/etc/hostsfilenano /etc/hostsand add a new line which contains ‘10.10.2.1 domain.com’
Hit-The-Dns with Dnsenum comparation
Some tools such as dnsemun does not always find the subdomains even if they exist in the DNS because of the way it implements threads and filters.
This post is licensed under CC BY 4.0 by the author.